Why your browser "connection is secure" information can be misleading
When you visit a website, the quickest way of verifying the confidentiality of your communication with the site is by checking to see if it is running on "HTTPS". In most cases, this could be sufficient especially when you consider that even free certificates provides as much security as the premium ones, lesser emphasis is usually placed on the certificate authority that issued the certificate and this is the gap that is used to break the sequence of communication between the victim and the web server, creating a man in the middle situation.
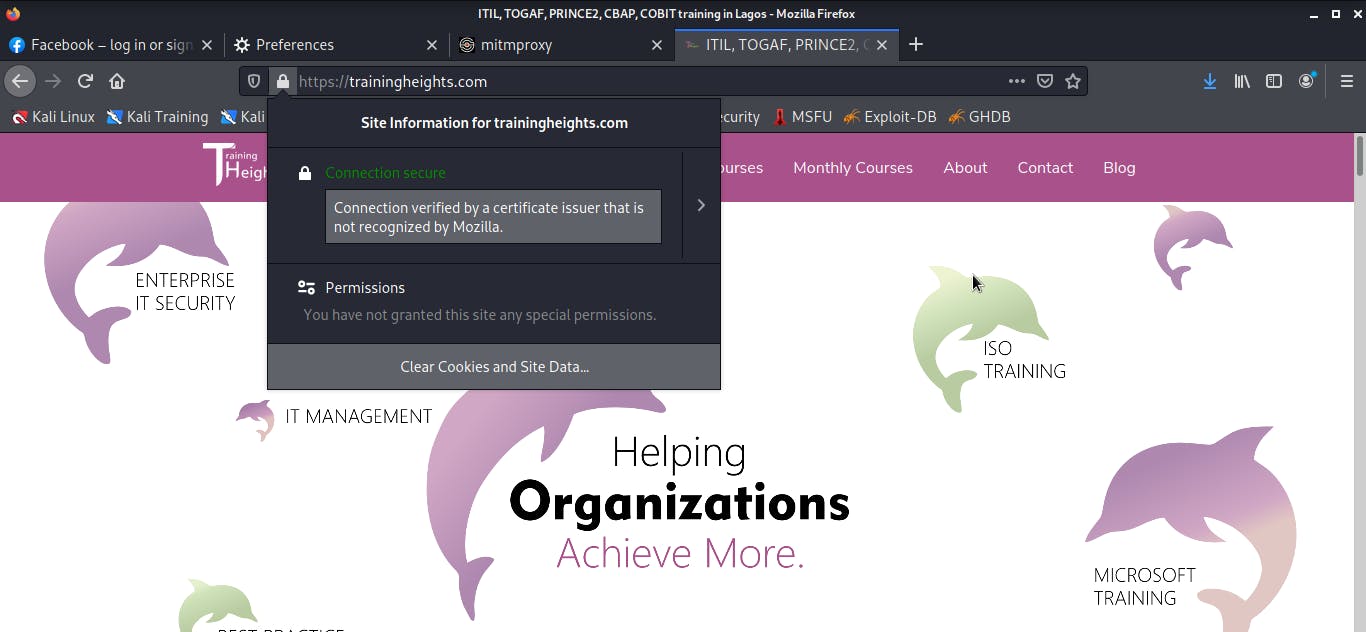 Connection is secure information by a malicious CA
Connection is secure information by a malicious CA
But before we get too technical and lose track of the topic of this article, the aim of this article is just to elucidate that when you direct your mouse pointer to the padlock in the address bar, and there is a "connection is secure" information, it is important to also look at the certificate authority that issued the certificate.
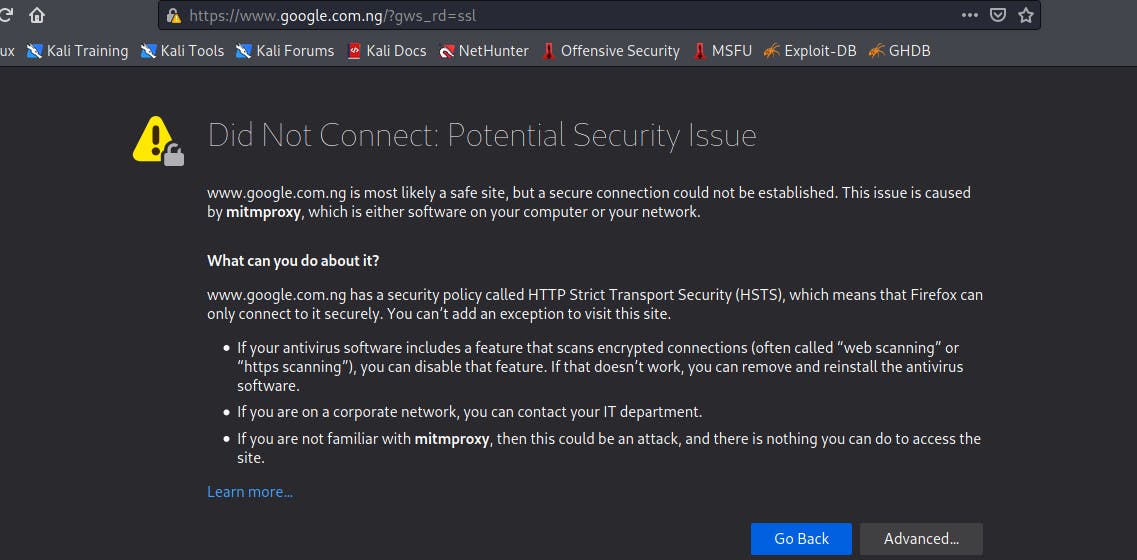 Lifting HTTPS from a site that has HSTS enabled
Lifting HTTPS from a site that has HSTS enabled
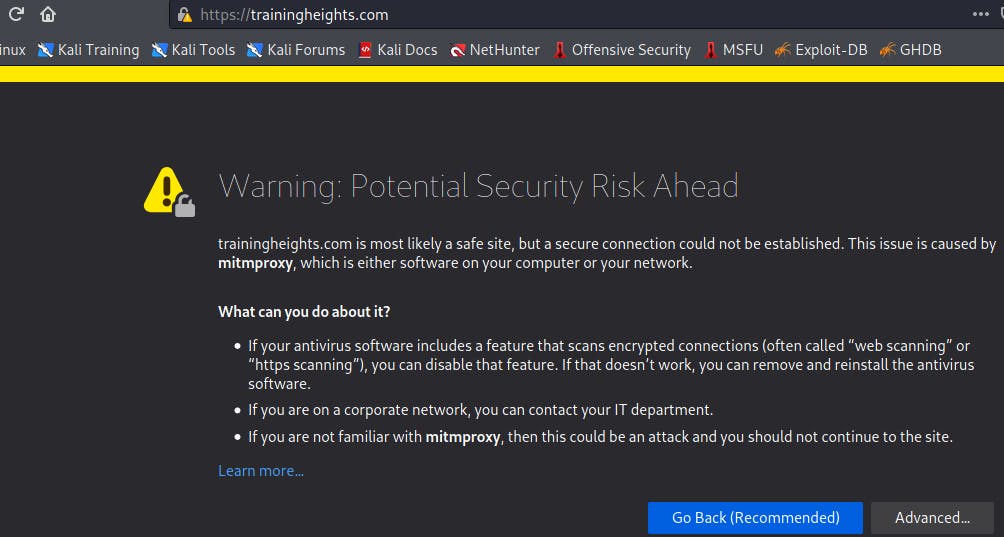 Lifting HTTPS from a site that does not have HSTS enabled
Lifting HTTPS from a site that does not have HSTS enabled
There are numerous tools that I use to exploit this, I will probably have a session hijacking series in the future, but I want to highlight three key points you should always remember when you are using a browser:
Websites that are running on HTTP implies that absolutely anyone on your network (or if a malware is already in the system) can monitor your activity (solution is to redirect all HTTP traffic to HTTPS)
If a web application redirects all http traffic into https, there are tools that can still exploit that redirection (solution is to enable HSTS)
The certificate authority can be refactored on a browser to give a misleading "Connection is Secure" notification (solution is to also check who issued the certificate)
if HSTS is enabled then an "HSTS hijack" tool could utilize DNS spoofing and forwarding to make the victim visit a lookalike and the webserver think attacker is the victim using captured victim's info (solution is to read links carefully before clicking on them)